Safeguarding your online privacy is more critical than ever. Temp mail forwarding has emerged as a powerful tool to combat spam, protect personal data, and maintain anonymity. This guide dives deep into how temporary email forwarding works, its benefits, top services, and best practices to maximize your security.
What is Temp Mail Forwarding?
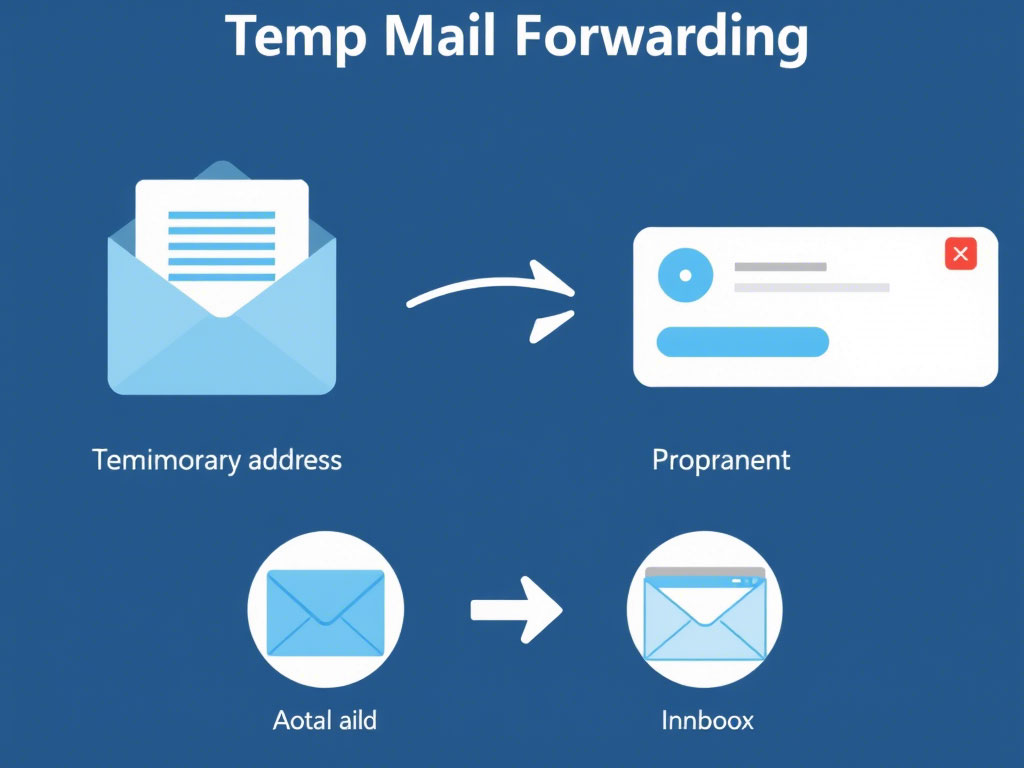
Temp mail forwarding (or temporary email forwarding) allows users to generate disposable, anonymous email addresses that automatically forward messages to a primary inbox. These addresses are short-lived, expiring after a set period or after a specific use case, ensuring your real email stays hidden from spam lists and data breaches.
How Does Temp Mail Forwarding Work?
- Generate a Temporary Address: Use a temp mail service (e.g., TempMail, Guerrilla Mail) to create a unique, randomized email.
- Forward Emails Automatically: Messages sent to the temp address are redirected to your primary inbox.
- Automatic Expiration: The address self-destructs after a predefined time (e.g., 24 hours) or once its purpose is fulfilled.
This process shields your real email from exposure, reducing the risks of phishing, spam, and identity theft.
Top Benefits of Using Temp Email Forwarding
- Spam Reduction: Keep promotional emails, newsletters, and junk mail out of your primary inbox.
- Enhanced Privacy: Mask your real email when signing up for websites, forums, or trials.
- Security: Prevent data breaches by using disposable addresses for low-risk accounts.
- Convenience: No need to manage multiple accounts—forwarded emails land in one place.
- Anonymity: Protect your identity during surveys, downloads, or anonymous interactions.
Common Use Cases for Temporary Email Forwarding
- Website Registrations: Sign up for apps, newsletters, or free trials without revealing your primary email.
- Online Shopping: Avoid marketing spam after making e-commerce purchases.
- Public Forums: Participate in discussions without exposing personal details.
- Beta Testing: Safeguard your inbox when testing new platforms.
- One-Time Downloads: Access resources (e.g., eBooks, software) risk-free.
6 Best Temp Mail Forwarding Services in 2025
- TempMailTurbo: Offers instant, anonymous addresses with 24-hour forwarding.
- Guerrilla Mail: Features unlimited disposable emails and optional extensions.
- 10-Minute Mail: Creates self-destructing addresses ideal for quick verifications.
- Forward Email: Custom domain aliases with permanent forwarding options.
- AnonAddy: Open-source service with encryption for heightened security.
- Burner Mail: User-friendly app with customizable expiration times.
Best Practices for Secure Temp Mail Forwarding
- Avoid Sensitive Data: Never use temp emails for banking, healthcare, or critical accounts.
- Check Expiration Dates: Ensure the address lasts long enough for verification emails.
- Use Reputable Providers: Choose services with SSL encryption and no-logs policies.
- Combine with a VPN: Boost anonymity by masking your IP address.
Temp Mail Forwarding vs. Disposable Emails: Key Differences
While both protect privacy, temp mail forwarding adds a layer of convenience by redirecting emails to your primary inbox. Traditional disposable emails (e.g., throwaway accounts) require manual checks, making them less efficient for time-sensitive tasks.
FAQs
Q: Is temp mail forwarding legal?
A: Yes, as long as it’s not used for fraudulent activities.
Q: Can I recover a deleted temp address?
A: No—once expired, the address and its emails are permanently erased.
Q: Are forwarded emails encrypted?
A: It depends on the provider; opt for services offering HTTPS and PGP encryption.
Conclusion
Temp mail forwarding is a must-have solution for anyone prioritizing online privacy and inbox cleanliness. By leveraging disposable email addresses with forwarding capabilities, you minimize spam risks, protect your identity, and streamline digital interactions. Choose a trusted provider, follow best practices, and take control of your email security today!